The 2016 Toronto Reel Asian International Film Festival has come to a close after a successful run from 8th to 19th November, 2016. As the largest Asian film festival in Canada, Reel Asian has been bridging the Pan-Asian contemporary cinema and Canadian community through creating a platform for emerging and award-winning directors, actors and the local community to share their work and opinions on films. This year, over half of the film titles were directed by North American filmmakers.
This year marked the 20th anniversary, and for the first time new elements were introduced for the film festival– including Reel Asian’s inaugural WEE ASIAN Kids Programme for parents and children, free entries to 10 films for senior and student audience, as well as a new 20/20 Interview Series. 20 candidates who either have worked or attended the film festival in the past 20 years were invited to talk about their memorable stories with Reel Asian, as well as the impact of the film festival on their lives.
Psiphon is very excited to collaborate with Reel Asian for the first time in celebration of their 20th anniversary. As much as the festival is a huge success itself with higher than before ticket sales, we helped expand their online exposure to our users in Canada and China, which received over 2.3 million views over the course of the festival. Through Psiphon’s content delivery, our users from China learned about media arts that were screening overseas. Psiphon users in Canada and China were also able to watch trailers of selected films on Psiphon Today.
Since our previous partnership with BFI Film Flare Film Festival, Psiphon continues to pursue opportunities to support art and cinematic initiatives. We are more than happy to connect our users to media arts that are relevant to them and provide an open platform for them to engage with the events.
Toronto Reel Asian International Film Festival will happen again in November 2017 with great films!
Check out this year’s Reel Asian Award winners and more festival highlights at www. reelasian.com
Want to collaborate with Psiphon Inc. for your next event? Email us at info@psiphon.ca
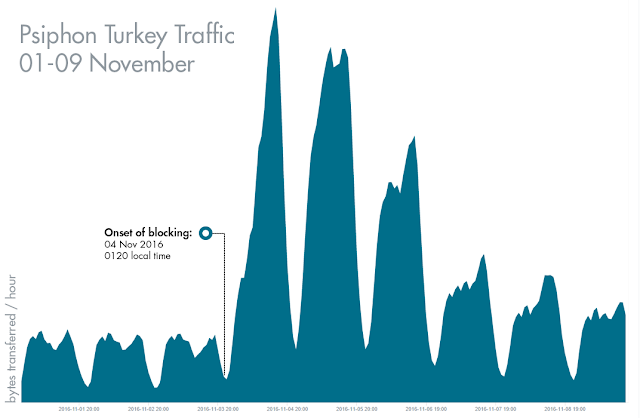
Following the detainment of 12 pro-Kurdish
lawmakers from the Peoples’ Democratic Party (HDP) in the early hours of November
4th, Facebook, Twitter, Instagram, YouTube, WhatsApp and Skype were blocked in Turkey. There were reports that Turk
Telekom internet provider completely disabled access to the internet or throttled
the connection to the point that it was impossible to connect.
Despite lack of official decision about the restrictions, and BTK’s
explanation that there was a technical problem throughout Turkey, Prime
Minister Binali Yildirim made a statement
later in the day and said “For security reasons, these kinds of measures can
be taken time to time. These are temporary measures. Everything goes back to
normal after the danger is eliminated.”
Social media and internet bans ended the following evening in most of the
country, but there were still some short-term connection problems during the
weekend in some regions, and it was reported that some Turk Telekom users did
not have internet for longer periods.
On the same day, multiple local outlets reported that Turkey’s
Information and Communication Technologies Authority (BTK) ordered internet
providers in the country to block censorship
circumvention tools, including Psiphon. Despite the rumor, Psiphon saw no
indication that its services were affected negatively.
The BTK denied that circumvention tools were ordered blocked; however
Ahment Arslan, the Minister of Transport, Maritime and Communication, said “We
only restrict the use of VPNs because of terrorism reasons. Surely nobody would
have an objection about this.”
The weeklong regional school took place at the Asian Institute of Technology (AIT), where more than 30 participants from various countries in Asia Pacific came together to share their experience and knowledge on the Regional Internet Governance issues. Organized by the Internet Education and Research Laboratory (inTERLab), the five-day workshop featured keynote speakers from various backgrounds such as international organizations, academic institutes, civil society, government and business sectors. These organizations include: Internet Corporation for Assigned Names and Numbers (ICANN), Electronic Frontier Foundation (EFF), Asia-Pacific Network Information Centre (APNIC), Korea Advanced Institute of Science and Technology (KAIST), OpenNet Korea and Com First India.
As a software company that develops a trusted tool that enables unrestricted Internet content access, Psiphon was very excited to share its feedback on Internet Governance issues, including the improvement of public awareness on Internet content freedom in the Asia Pacific Region. We were extremely happy to connect with established users, within the school, to collect and understand feedback provided in regards to our software. Furthermore, Psiphon built relationships with new users from South and Southeast Asian countries, such as Thailand, Pakistan and Philippines. During the role-play workshops, Psiphon contributed to the final report on the facilitation of new Internet users in the next decade. This report is now available on the APSIG official website at apsig.asia.
APSIG is a pilot program envisioned by Dr. Kilnam Chon and the next APSIG will also be hosted in Bangkok, Thailand.
Want to invite Psiphon Inc. to your next event? Email us at info@psiphon.ca